Security & SIEM
Complete End-to-End Security Solutions with Security Analytics & Log Data Analysis with Regulatory Compliance

The OpenSource Security Platform
VL Cloud will offer an free, open source and enterprise-ready security monitoring solution for threat detection, integrity monitoring, incident response and compliance.
Why OpenSource ?
Flexible, scalable, vendor-free lock and license-free. Trusted by thousands of enterprise users also have support from free community.
Endpoint Detection and Response (EDR)
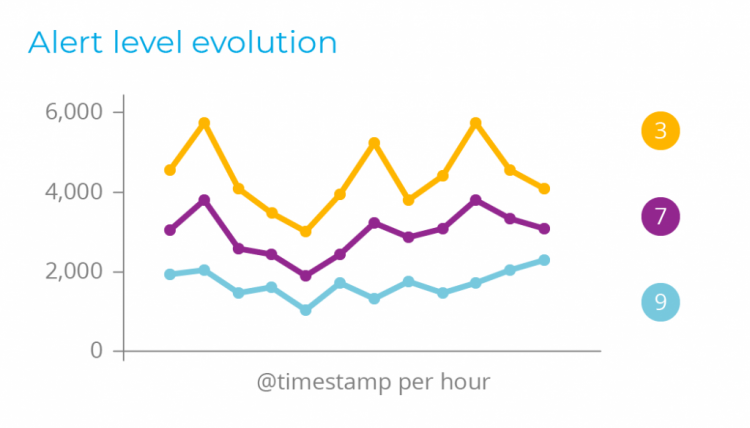
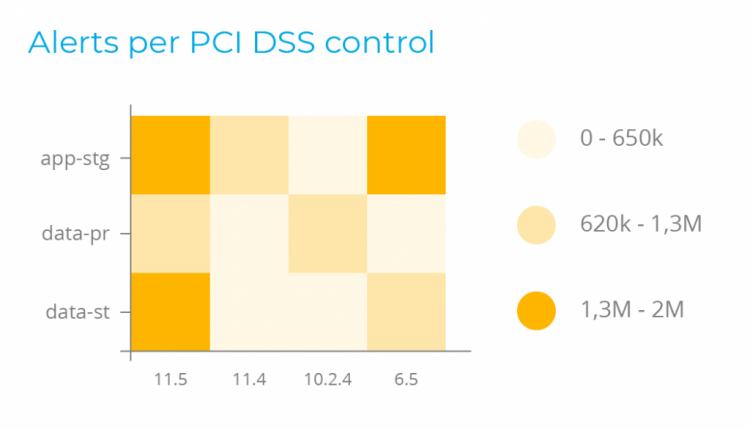
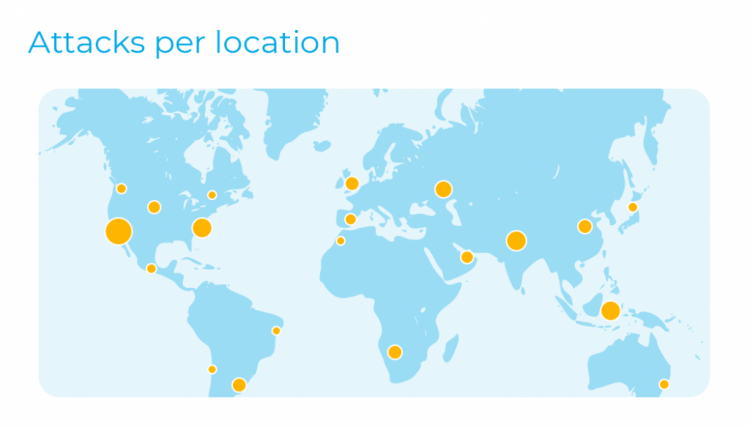
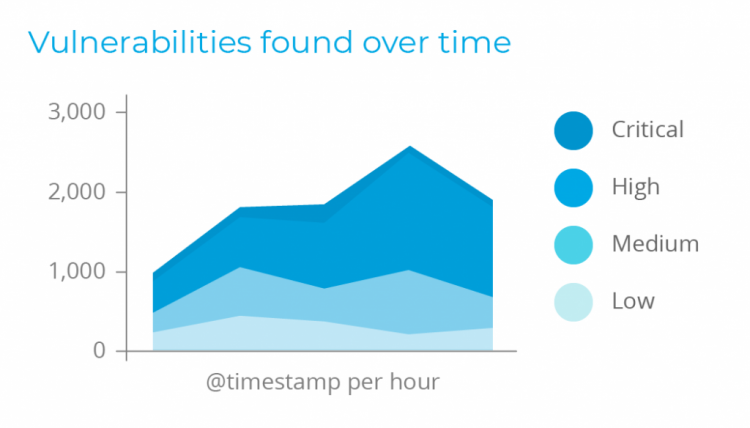
VL Cloud deals with the requirement to monitor and respond continuously to advanced threats. It focuses on giving the right visibility to help security analysts identify, investigate and respond to threats and attack camps on various endpoints.
VL Cloud detects hidden exploit processes that are more complex and can be used to circumvent traditional antivirus systems than just a simple signature pattern. The VL Cloud also offers active response capability to block a network attack, stop the malicious procedure, or quarantine an infected malware file.